* ClipCaster
 [ Update: I no longer have time to continue to improve this app. Thanks to everybody who tried it out and improved awareness of this vulnerability! Improvements & fixes are welcome via Github ]
[ Update: I no longer have time to continue to improve this app. Thanks to everybody who tried it out and improved awareness of this vulnerability! Improvements & fixes are welcome via Github ][ LastPass update round 2: I automated the exploit for Facebook, as described in my blog post. If LastPass changes things up again it will stop working and may take a few days to get back up, but hopefully this time they will realise how ineffective this is and stop exposing their users to this vulnerability. ]
[ LastPass update: ClipCaster no longer automates the retrieval LastPass credentials. LastPass' fill-in is still vulnerable though. For an explanation of why, and how to verify it yourself (some knowledge of JavaScript required), see my blog post at https://blog.xbc.nz/2014/12/lastpass-attempt-at-client-side-android.html ]
ClipCaster is an open source proof of concept app that shows how any installed app can read passwords when they're used from password management applications.
It can also be used as a tool to track the state of the clipboard, and to get a dump of the JavaScript LastPass uses for its Chrome Fill-In feature.
Ars Technica article: http://ars.to/1vwcmT0
Finds credentials when using RoboForm's 'fill-in' feature for Chrome (Android version at least 4.3) and KeePassDroid.
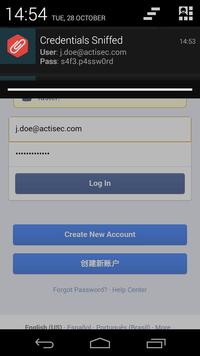
We do NOT store the passwords or send them anywhere; this app does not even have the Internet permission. The only place they are used is in the notification when they are sniffed.
Now on the open source app store, F-Droid: https://f-droid.org/repository/browse/?fdfilter=clipcaster&fdid=com.actisec.clipcaster
===
Scope of ClipCaster
===
ClipCaster will automatically detect credentials when used from RoboForm filling out fields in Chrome (thanks to Robert for the tipoff) and KeePassDroid's copying notification.
ClipCaster also has a clipboard history, collected while the app is switched on. Just hit the 'history' icon on the main app. With this you can see what any app is doing with the clipboard.
In the case of LastPass, it will also aid manual reproduction of the vulnerability by providing the JavaScript dump and the time it was generated. See https://blog.xbc.nz/2014/12/lastpass-attempt-at-client-side-android.html for an example
===
Scope of vulnerability
===
For all password managers: if it requires you pasting your credentials, it is vulnerable. If the manager has a built-in browser or keyboard, using that feature will almost definitely avoid the vulnerability. If the manager doesn't, type passwords manually to avoid the vulnerability
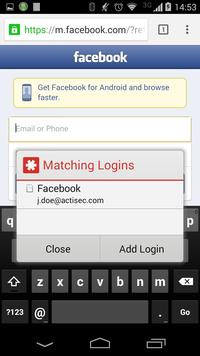
For LastPass: Even though it doesn't mention it, the 'fill-in' feature (the one that pops up with credential choices, as in the screenshots) uses the clipboard and so is vulnerable. The alternatives are: the LastPass keyboard (or input method as they call it), the built-in browser, or using a mobile browser with a browser-specific LastPass extension such as Dolphin.
If you're unsure whether a password manager's feature is vulnerable, ask the developers of the password manager. Alternatively, email x.clark@actisec.com and we will attempt to check it out.
===
Permissions
===
No permissions required
===
Source & Acknowledgements
===
https://github.com/activems/clipcaster
This project is an independent implementation of the concept in "Hey, You, Get Off of My Clipboard - On How Usability Trumps Security in Android Password Managers" (http://fc13.ifca.ai/proc/4-2.pdf).
A special thanks to Arturo Blas-Jim?nez, Daniel Resnick and Andrew Wilson for testing and to Valerio Bozzolan for the Italian localisation.
If any bugs are found, please put a description of them plus your version of Android on the issues page of the GitHub repo (https://github.com/activems/clipcaster/issues) or email x.clark@actisec.com
Recent changes:
Wishing everyone a safe and secure Christmas and New Years!
Limited LastPass credential interception is back! Works for Facebook (English and Italian) sites, many more sites to be added soon. If LastPass changes things up again it will stop working and may take a few days to get back up, but hopefully this time they will realise how ineffective this is and stop exposing their users to this vulnerability.
Content rating: Everyone
Author: Active Mobile Security
Version: 1.0.60
Market link: com.actisec.clipcaster
Web site: http://nowebsitefound
Source code:
Code license:
Market downloads: 1,000-5,000
Market rating: 4.3 / 5.0
Category: Top:/Applications/Education
Added: 2015-06-17
Updated: 0000-00-00
Hits: 683



